- Firefox Ssl_error_weak_server_ephemeral_dh_key
- Ssl_error_weak_server_ephemeral_dh_key Chrome
- Tomcat Ssl_error_weak_server_ephemeral_dh_key
Quick Guide To Fix Error Message: err_ssl_server_cert_bad_format
Google chrome is one of the popular and widely used web browsers throughout the globe. Many users rely on it, and it’s no exception that sometimes unwanted error messages do occur when someone tries to open the website. Some are common, and some are quite unheard such as err_ssl_server_cert_bad_format- Your server is using weak Diffie-Hellman keys and might thus be affected by the Logjam attack. Because of this attack more and more browser and TLS stacks increase their minimum length of the DH key to 768 or 1024 bit. Probably the OpenSSL version you are using in your server uses a 512 bit DH key by default, which is too small.
- The latest versions of Firefox (39+), Thunderbird (38+) and Chrome (45+) have implemented new security measures that block websites with older, insecure SSL certs. This is to protect against the '.
- Firefox 39 and the Firefox 31 and 38 ESR releases upgrade the TLS implementation NSS to version 3.19.1. To harden the browser against Logjam attack the minimum key length for DH parameter within the TLS handshake is now 1023 bits.; Older versions of Confluence (eg. 4.0.3) are bundled with a version of Tomcat that uses key lengths that do not meet the minimum.
(In reply to:Gijs Kruitbosch from comment #16) (In reply to f0rhum from comment #15) Although the thread title was changed by some admin Aside: I am not a BMO admin.I changed the title to be solution-oriented. Sorry Gijs, I didn't want to be rough. As I saw what how wrote and I couldn't edit my post I just didn't check if anybody can change the title.
If you think what does this error message means or how to solve it, then you’re not alone. It’s not an error that is seen often, so it’s quite apparent that you might question how come this error message occurred.
Let’s get into details.
What Does This Error Message: err_ssl_server_cert_bad_format Means & What causes it?
It’s one of the SSL based errors that occurs whenever you try to visit a website that has a self-signed SSL/TLS certificate installed instead of an SSL/TLS certificate provided by trusted Certificate Authority such as Sectigo or Comodo.SSL/TLS Certificates provided by known certificate authorities are called trusted, and it’s accepted globally by all the popular web browsers like Google Chrome and Mozilla Firefox.
How to Solve This Error Message: err_ssl_server_cert_bad_format?
There’s a solution, but it’s temporary.Firefox Ssl_error_weak_server_ephemeral_dh_key
To solve this issue, follow the below steps:
Ssl_error_weak_server_ephemeral_dh_key Chrome
You can also try this option through the web browser. For example, in Google Chrome,Click on three dots at the top right corner and click Settings.
Though, if you’re in doubt whether to go with the paid one or not from SSL/TLS certificate providers like RapidSSL, Sectigo, or Comodo, then there’s one more option of getting a free trial before making any final decision. For example, RapidSSL CA offers an SSL Certificate as a 30-day trial free of cost.
ERR_SSL_WEAK_SERVER_EPHEMERAL_DH_KEY
Yeah, this is one of the new features coming with the latest version of Google Chrome (45). It basically means that the most used browser is becoming unusable to manage older Cisco products. I faced the problem when I was trying to access one CUCM version 9.x in my lab.
I'm pretty sure there are thousands of products working pretty fine sitting in your private LAN behind a firewall, but you simply cannot use Chrome to access them as all of them require https. I've spent probably half a day looking for a workaround in Chrome but so far I wasn't able to find such.
The message in the browser is saying 'This error can occur when connecting to a secure (HTTPS) server. It means that the server is trying to set up a secure connection but, due to a disastrous misconfiguration, the connection wouldn't be secure at all! In this case the server needs to be fixed. Google Chrome won't use insecure connections in order to protect your privacy.' There is even a link with more instructions about how to fix the problem but all of them are asking you to do the changes on the server side. Well, thanks for that but I simply cannot do it, as Cisco's back end is pretty much closed for changes. Honestly, I think this time Google overdid it!
The 'fix' in the browser is related to a well known security attack called Logjam. You can find more details about it here (https://weakdh.org/).
Workaround for Google Chrome
So, you have some old Cisco product that you cannot access with Google Chrome. What to do now? You have to create new shortcut for your Chrome adding the following startup parameter:
'C:Program Files (x86)GoogleChromeApplicationchrome.exe' --cipher-suite-blacklist=0x0039,0x0033
By doing this you are allowing the weak Diffie-Hellman public keys - TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x33) and TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) which is absolutely enough to be able to access your Cisco environment with Google Chrome.
Workaround for Mozilla Firefox
When I switched from Firefox to Chrome as a primary browser couple of years ago, I did it with some reserves. And here it comes probably the biggest proof that Firefox is much more mature browser. Mozilla Firefox has the same fix (Error code: ssl_error_weak_server_ephemeral_dh_key) as Google Chrome and it was even released couple of weeks earlier but together with that there is a workaround by modifying some of the advanced settings. Here is a step-by-step guide of how to do that.
Tomcat Ssl_error_weak_server_ephemeral_dh_key
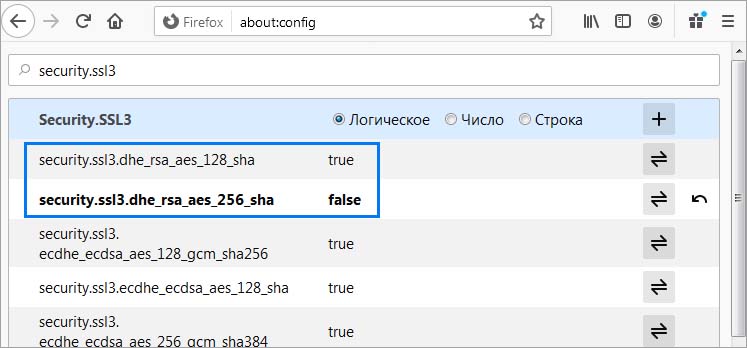
Open your Firefox and type in the address bar about:config. There will be a warning message so you will have to promise that you will be careful.
Once you open the advanced configuration section, type in the Search field ssl3. Change the values of security.ssl3.dhe_rsa_aes_128_sha and security.ssl3.dhe_rsa_aes_256_sha from true to false by simply double clicking on them.
That's it! Now you can use Firefox to access your devices which are still running weak Diffie-Hellman ciphers.
